ESL_Home: CALL resources main page | Site Index
About: Vance | Vance's papers and presentations | Blog: AdVANCEducation
![]() Save this page to your DEL.ICIO.US account and TAG it
there
Save this page to your DEL.ICIO.US account and TAG it
there
ESL_Home: CALL resources main
page | Site Index
About: Vance |
Vance's papers and presentations | Blog:
AdVANCEducation
|
Viruses, Worms, Trojans:
|
This is NOT a hoax ...
What's WRONG with this picture??Thank you Melencio, but, no, I don't think I'll double click on your attachment and unleash your Visual Basic script on my computer. Thank you so much for thinking of me though, whoever you are ... |
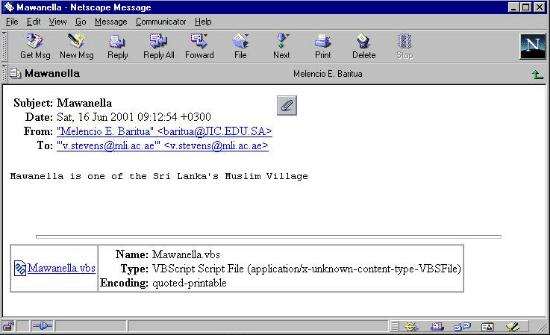 |
| Here's another one: Do you think the FixKlez.com is
legit? TrendMicro.com is where valid email is sent from that company, but has
this address been spoofed? Confirmation of that was quickly followed a Norton
AV report indicating that the attachment had been quarantined. Don't ever launch an executable attachment that arrives in your email inbox! (From anybody). Executables have extensions like vbs, com, exe, pif ... |
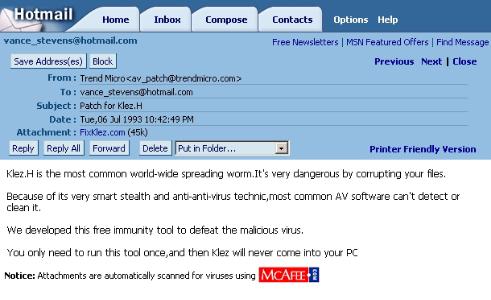 Incidentally, this was received on Feb 5, 2003. Check the date of this email! |
Here are my personal strategies for virus protection (note, these are a little dated in specifics, but the general strategies for avoiding problems from the Internet are still sound I believe - Vance, 2006).
This site had a comprehensive listing free software which was being maintained and updated in January 2007, including annotated sections on firewall, antivirus, and anti-spyware - Bear Bottoms Open Source and Freeware Research: http://bearbottoms1.com/
It is not enough to simply install a current virus checking program and forget about it. 'Current' ceases to apply whenever the next virus is propogated. You must protect yourself by frequently downloading and installing virus signature updates. These are data files the virus checker uses to identify certain tell-tale strings that are unique to known viruses. Obviously, when new viruses are written, your signature files need to be updated so your virus checker can find them. Because of these signature files, you usually can't run more than one virus checker on one computer. One virus checker might set off alarms if it finds what it's looking for in the signature files of competing virus checkers. So un-install existing checkers before installing an new one.
What happens if you find a virus? If you've got the name of the virus then key that into Google and your best bet is probably Symantic's detailed instructions on how to remove them. The process, which is explained on Semantic's site in exact detail with screen shots, is something like:
- disable system restore (otherwise you risk restoring your sys with virus)
- update your virus signatures
- enter safe mode
- run virus scan to locate where the critter is
- delete the critter AND
- Symantic tells you how to get into the registry and for any particular virus which keys to look for and delete
If you can't do 1 to 4 because you're not running a/v software you can at least do 5 and 6. If you don't do 6 then you'll likely be revisited.
Some attachments try to fool you by taking advantage of the default setting in Windows which hides extensions from you. For example, in the case of something.TXT.pif, if you had accepted the Windows default setting this file would appear to you as something.TXT and you might have a look, thinking how can a TXT file harm me? But this one is something.TXT.pif. TXT is part of its name, not its extension. You can see the full extension of all files by clicking on View / Folder Options in any window, click the View tab, and make sure that "Hide extensions of known file types" is NOT checked. <-- This is very important. Do it right away! Remember, the default setting on Windows is to check IN this option. Therefore you have to UNcheck it in order to see the extensions on files that people send you as attachments.
If I think I really need the attachment, I email it to myself at the office where we keep a corporate version of Norton updated frequently, and I open it there.
It is dangerous to send attachments on lists. There are viruses, worms, and trojans that will get into someone's address book and send messages to everyone in that address book, and send as an attachment a program that will install itself on the recipient's computer.
Here are some antivirus programs that I have used or seen recommended:
On 26 Nov 2006 a webhead recommended this anti virus shield from AOL, saying "It's free and very effective. Updates definitions on a daily basis. It needs to be activated which just means you give them your email address and they send you an activation password which you paste into the software and that's it. http://www.activevirusshield.com/antivirus/freeav/index.adp?
In Jan 2007 a Knowmate recommended an impartial brower check for spyware (not trying to sell you firewall software: "Browser Security Test." http://bcheck.scanit.be
AntiVir - free at: http://www.free-av.com
AVG Anti-Virus Free Edition is a free anti-virus protection tool developed by GRISOFT for home use. from http://www.avast.com. Click on Desktop solutions and then Free Software. Why free? According to this page: http://www.avast.com/eng/free_software.html - "avast! 4 Home Edition is a full-featured antivirus package designed exclusively for home users and non-commercial use. Both of these conditions should be met! Our company offers the Home Edition free of charge, since, in our opinion, it is possible to avoid global virus spreading by efficient prevention; however, many user are not able to or do not want to pay for antivirus software." This information was posted July 14, 2006. - Update 26 Nov 2006 regarding confusion in the Webheads list over whether the free version had been discontinued: "a new version has come out, 7.5 . Current users of the free product were sent a letter and the link in the letter led to the paid version which they would like to have you buy. You have to do quite a bit of searching to find the free version link: http://free.grisoft.com/doc/avg-anti-virus-free/lng/us/tpl/v5"
BitDefender - rated highly in Webheads list email Jan 1 2008
Command AntiVirus Software, according to a Neteach-l posting, "is one of the leading anti-virus research organizations in the world. The Command Anti-virus product has been tested and certified by more third-party testing groups than any other anti-virus product." http://www.commandcom.com - I have used this software and found it reliable when it was Frisk Software's F-PROT (Vance)
Computer Associates, Innoculate It used to be free antivirus software with free updates and support according to the website at: http://antivirus.ca.com/. This program was recommended on lists I followed c.2001, and it used to allow free updates to its virus signature files (the files the computer needs to check for the latest viruses, which you download from the website and install on your computer as often as possible). Being a company with a conscience, they still allow free updates to people who got their foot in the door with their beta products, but if you haven't got an account with them already you now have to pay a little something for their services.
McAfee's http://www.mcafee.com/anti-virus/default.asp?
Network Associates' VirusScan, http://www.mcafee.com/. You can purchase software, subscribe to a protection service, or check your PC online for viruses here. You can also get on the Dispatch mailing list here (put you on a mailing list for virus alerts; worth having; Vance)
NOD 32 Antivirus Program - http://www.nod32.com - free download available in trial version; purchase - single home user $39 with discounts to educational and non-profit organizations
Solomon's
Symantec Norton Anti-Virus at http://www.symantec.com/
TrendMicro at http://www.antivirus.com has an online virus detection facility called "House Call" at http://housecall.antivirus.com/explorer.html or (April 2003) http://housecall.trendmicro.com. It has versions of its site in Chinese, Japanese, German, Spanish, etc. It also has a newsletter with its latest info on viruses etc and hoaxes: http://www.antivirus.com/trendsetter/virus_report/
Zone Alarm - http://www.zonelabs.com/; according to a Jan/Feb 2001 Neteach-l posting, ZoneAlarm is, "deservedly, the best known and free for personal use." Zone Alarm's forte is intrusion protection for those who keep Internet connections open all the time. From the web site it is not clear if it provides signature updates for free users.
About.com's page on AntiVirus software: http://antivirus.about.com/compute/software/antivirus/library/weekly/aa111099.htm
Internet Society's collection of information about viruses and hoaxes includes the latest threats, tips on how to avoid being infected, how to get rid of a virus, and general information about viruses, worms, trojan horses, etc.- http://www.isoc.org/internet/issues/security/
Did you know you can contract the KAK worm and FUNLOVE simply by browsing the Web? Here is the SANS Institute site that describes the problem and the cure: http://www.sans.org/newlook/alerts/virus.htm
To quote the text at the above site (October 2000):
"Email viruses are now spreading WITHOUT THE USER OPENING ANY ATTACHMENT. Personal computers running Internet Explorer (IE) version 5.0 and/or Microsoft Office 2000 are vulnerable to virus attacks using most HTML-enabled email systems, even if the email recipient opens no attachments. You don't even have to use IE; just have it installed with the default security settings. If you have not closed the hole, you can receive viruses (and spread them) by viewing or previewing malicious email without opening any attachment, or by visiting a malicious website. The problem is caused by a programming bug in an Internet Explorer ActiveX control called scriptlet.typelib. This is by far the fastest growing virus distribution problem and ripe for a hugely destructive event - at least as large as the ILOVEYOU virus. Updating your virus detection software, while important, is not an effective solution for this problem. You must also close the hole. The hole can be closed in five minutes or less using tools available at Microsoft's security site:
http://www.microsoft.com/security/bulletins/ms99-032.asp
The correction script may be run directly from:
http://www.microsoft.com/msdownload/iebuild/scriptlet/en/scriptlet.htm"
Graham Davies maintains a couple of useful urls on viruses, and another problem with what he calls 'dodgy links'.
BadTrans
Info from Symantec, including removal tool: http://securityresponse.symantec.com/avcenter/venc/data/w32.badtrans.b@mm.removal.tool.html
BadTrans is a low damage but prolific trojan going around in Nov/December 2001: http://securityresponse.symantec.com/avcenter/venc/data/w32.badtrans.b@mm.html
Prevention: According to the above web site, do not open any email that has an attachment in which the second extension is .pif or .scr. Any email that has such an attachment should be deleted.
McAfee info:
W32/Badtrans@MM is a mass-mailing worm that drops a remote-access Trojan. The virus arrives via the Microsoft Outlook email program and attempts to send itself by replying to unread email messages.
The email may contain the text "Take a look to the attachment" in the message body and will contain an attachment that is 13,312 bytes in size. The attachment name is created in three sections, for example, card.doc.pif.
For detection and removal instructions for the W32/Badtrans@MM virus, click here. ===> http://clinic.mcafee.com/clinic/ibuy/campaign.asp?cid=2608
Take note of the email below ...
Notice that the return address has an underscore in it. When you reply, the message will bounce back to you. Under no circumstances open the attachment.
Subject: Re: You have been added to mli
Date: Wed, 28 Nov 2001
13:10:10 +0400 (GST)
From: John Doe <_j.doe@somewhere.com>
<-- Note the _underscore>
To:
vstevens@emirates.net.ae
-------------------------------------------------------------------
Graham Davies posted the following on EUROCALL-MEMBERS@JISCMAIL.AC.UK
Dear Colleagues
Watch out for a new version of the Badtrans trojan, which has been on the rampage for the last few days. I've received it six times since Friday 24 November. See my "bugs" page under the heading "W32.Badtrans.B@mm" for further details:
http://www.camsoftpartners.co.uk/bugs.htm
This from a friend in Oman, who passed on his experiences removing the virus from his computer.
I have got many messages back about this virus, and from the pattern, I have concluded that:
When attacking the problem, the first thing to do is to update your anti-virus program with the latest virus definitions. next step you should find the file KDLL.DLL and try and remove it. You will need to go into DOS. Then scan your computer for virus (it takes long time).
I have Norton Antivirus program, and the total virus scan of my computer did not pick up the virus from my Outlook Express Inbox, but it did when I scanned the Inbox separately.
CIH, April 26, Chernobyl Virus
CIH destroys a meg of data on your hard drive rendering it practically useless.
You would get this virus only by running infected executable files, such as those that come with email attachments or from a borrowed floppy. The virus program runs on your system and checks the date. When it sees April 26, it triggers. A version of it triggers on the 26th of any month.
To prevent this virus, you must have a version of a virus checker or its updated virus signatures dating later than July 1998.
"The CIH virus (a.k.a. "Chernobyl") originated in Taiwan in early June1998 and hits on the 26th of each month. The most prevalent and dangerous form of the virus, CIH 1.2, appears once a year on April 26, the anniversary of the Russian nuclear accident.
CIH can destroy a hard drive by overwriting the first 1 MB of each hard disk on the system. It can also eliminate the ability for the computer to start up by overwriting some flash_BIOS chips and rewriting them with garbage."
CIH affects Win95/98 machines. It does not affect NT.
See also:
Happy99.exe
Internet worms are rife on the web as of early 1999. A particularly pernicious one is the happy99.exe worm that is spread in email attachments. This is not a hoax. If you get any email that contains any mention of happy99.exe then don't open any attachments associated with that email. When I get these, there isn't much message left in the sender's email, but if you do get a message, it doesn't hurt to read it or copy the text somewhere. Just don't run any programs that came with the email. For more information see:
On 27 Mar 1999, there was an informative message regarding this worm posted on calico-l. Here are exerpts from the text, most of which is taken from the Symantec page:
DO NOT try to execute the attached file!!!!! Your machine won't blow up, but you will have to do all the following steps.
IF YOU HAVE NOT tried to open the attached file, then just delete it and throw out the trash. Use 'Find File' to insure that the attachment was truely deleted from your disk.
Description: This is a worm program, NOT a virus. This program has reportedly been received through email spamming and USENET newsgroup posting. The file is usually named HAPPY99.EXE in the email or article attachment. When being executed, the program also opens a window entitled "Happy New Year 1999 !!" showing a firework display to disguise its other actions.
The program copies itself as SKA.EXE and extracts a DLL that it carries as SKA.DLL into WINDOWS\SYSTEM directory. It also modifies WSOCK32.DLL in WINDOWS\SYSTEM directory and copies the original WSOCK32.DLL into WSOCK32.SKA. WSOCK32.DLL handles internetconnectivity in Windows 95 and 98.
The modification to WSOCK32.DLL allows the worm routine to be triggered when a connect or send activity is detected. When such online activity occurs, the modified code loads the worm's SKA.DLL. This SKA.DLL creates a new email or a new article with UUENCODED HAPPY99.EXE inserted into the email or article. It then sends this email or posts this article. If WSOCK32.DLL is in use when the worm tries to modify it (i.e. a user is online), the worm adds a registry entry
KEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce=SKA.EXE
The registry entry loads the worm the next time Windows start.
Removing the worm manually
1.delete WINDOWS\SYSTEM\SKA.EXE
2.delete WINDOWS\SYSTEM\SKA.DLL
3.replace WINDOWS\SYSTEM\WSOCK32.DLL with WINDOWS\SYSTEM\WSOCK32.SKA
4.delete the downloaded file, usually named HAPPY99.EXE
Safe Computing:
This worm and other trojanhorse type programs demonstrate the need to practice safe computing. One should not execute any executablefile attachment (i.e.EXE, SHS, MS Word or MS Excel file) that comes from an email or a newsgroup article from an unknown or a untrusted source.
Hybris Worm
On 11 Apr 2001, The Symantec website contained an article on the Hybris worm: http://www.symantec.com/avcenter/venc/data/w95.hybris.gen.html
According to the article, damage from the worm is considered relatively low. One of its manifestations is a a rotating spiral on the Windows desktop. The worm takes over a crucial system file Wsock32.dll and sends itself out in attachments to your email correspondents such as the one I received. If you are infected, NAV might be able to repair this file, but it doesn't always work (especially if you're connected to a network) so it might be necessary to reinstall certain files from the Windows installation CD. Instructions for removal are on the web page indicated above.
Melissa
This is one of a genre of "viruses" that attaches itself to your normal.dot template in MS Word. You get the virus by opening an infected attached Word document. Thereafter, your Word documents are infected until you clean or replace your normal.dot template. For more information see:
This is from a posting to TESLCA-L in February 2000
"... by running Napster, you can introduce serious security risks to your machine and the other files on it, as well as to other computers on the network. Napster disregards the security of individual computers in misleading ways that are unprecedented.
In the default configuration, when you download your first music file from Napster, you automatically also download Napster software that turns your computer into a file server. This software allows any other machine on the Internet to connect to your computer and download copies of your files without your knowledge or approval. Triggered by a request from the other machine, the Napster software on your computer then searches your hard drive and any mounted network drives for "music files to share."
Unprotected file sharing and file scanning create significant risks of compromise to your computer and your privacy, as well as to other computers on NYU-NET. There is no way to tell what malicious functions may be performed by the software you automatically download with the music or what modifications may have been made to the music files themselves. This security issue is further complicated by Napster's decision to release the source code for the software it downloads onto your machine. The resulting proliferation of authors and versions makes your machine even more vulnerable to unexpected intrusions.
Chief Information Technology Officer, New York University"
Pretty Park
The following was taken from the mcAfee virus W32/Pretty.worm.unp Help Center http://www.mcafee.com/viruses/prettyworm/, which is no longer an active page:
W32/Pretty.worm.unp is the unpacked edition of the original "W32/Pretty.worm" Internet worm. It was discovered on 2/15/00. On 2/23/00 AVERT upgraded its risk assessment from Low to Medium—On Watch, due to a significant increase in prevalence. On 3/2/00, in response to the worm's continued, rapid spread, AVERT once again upgraded its risk assessment to HIGH. W32/Pretty.Worm.unp infects Windows 95/98/NT systems.
W32/Pretty.worm.unp arrives via email from affected users who have also run this Internet worm. It appears as an attachment titled "Pretty Park.exe", with the icon of a character from the animated television series "South Park".
This worm will try to email itself automatically every 30 minutes to all email addresses listed in the Internet address book.
It will also attempt to connect to an IRC server and join a pre-determined IRC channel in such a way that the worm's author could use the IRC connection to retrieve such information as the computer name, registered owner, registered organization, system root path, and Dial Up Networking username and passwords.
From my own email April 23, 2000
Just in the event anybody was zapped by the Pretty Park virus recently circulated, here is a fix for it (you do this only if your machine is running the virus):
You have to remove the command from your registry before you can delete the offending file. Deleting the file first and then rebooting causes your registry to fall over in a heap while looking for the file it's trying to execute. So don't delete the virus file without removing it from your registry first.
A warning about your registry, a mistake here can turn your machine into silly putty. If you don't feel comfortable about following these instructions, find someone who can help out.
I'm not an expert myself, but the above technique has been used to remove Pretty Park from machines at our office.
VBS.LoveLetter.A
The following was sent out to ISP customers from Emirates.net.ae
"VBS.LoveLetter.A is an email worm, mIRC worm, and a file infector. VBS.LoveLetter.A will use Microsoft Outlook and email itself out as an attachment with the above subject line and attachment name. The body of the message will be "kindly check the attached LOVELETTER coming from me". The virus will also infect files with the following extensions: vbs, vbe, js, jse, css, wsh, sct, hta, jpg, jpeg, mp3, and mp2
The virus will insert the following files: MSKernel32.vbs in the Windows
System directory; Win32DLL.vbs in the Windows directory;
LOVE-LETTER-FOR-YOU.TXT.vbs in the Windows System directory;
WinFAT32.EXE
in the Internet download directory;
WIN-BUGSFIX.EXE in the Internet
download directory;
script.ini in the mIRC directory
More information is available from various anti-virus vendor websites:
VBS.NETWORK
See the Norton AntiVirus Enclyclopaedia at: http://www.symantec.com/avcenter/venc/data/vbs.network.html
The main symptom of VBS is that you find multiple copies of the Windows NETWORK.VBS program on your hard disk. One copy is supplied with Windows and is genuine. It appears in the Windows/Samples/WSH directory. If you find any other copies on your hard disk then they may harbour viruses. Check the above URL at the Norton site for information on how to remove them. (reported by Graham Davies, 13 Sep 2000)
W32.HLLW.Qaz.A
See the Norton AntiVirus Enclyclopaedia at: http://www.symantec.com/avcenter/venc/data/qaz.trojan.html
The main symptom of W32.HLLW.Qaz.A is that it replaces the Windows NOTEPAD.EXE program in the main Windows directory with one containing the virus, renaming the genuine NOTEPAD.EXE program as NOTE.COM. If you find NOTE.COM on your hard disk, check the above URL at the Norton site for information on how to remove the virus. (reported by Graham Davies, 13 Sep 2000)
W32/Naked@MM
This was sent out to McAfee.com Dispatch Subscribers in March 2001
Since its discovery early on March 6, 2001, McAfee.com has seen a large and growing number of computers infected with W32/Naked@MM. This is a HIGH RISK virus that is spreading rapidly via the Windows email program Outlook. The infected email can come from addresses that you recognize. Attached is a file named NakedWife.exe, which poses as a Flash movie. The email message can appear as follows:
When run, it copies itself to a TEMP directory and displays a window entitled "Flash" which reads "JibJab loading". It then attempts to delete all .BMP, .COM, .DLL, .EXE, .INI, and .LOG files in the WINDOWS and WINDOWS\SYSTEM directories and emails itself to all recipients in the Windows Address Book using Microsoft Outlook.
For detection and removal instructions: http://clinic.mcafee.com/clinic/ibuy/campaign.asp?cid=2163
Do you get messages like this from people you know and trust? Don't open the attachments! The email addresses are spoofed.
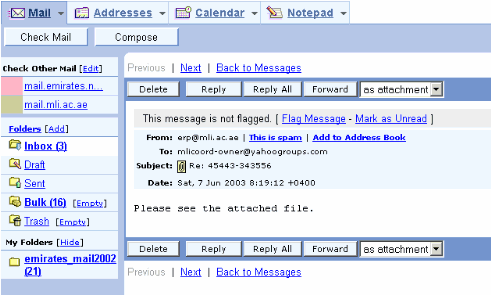

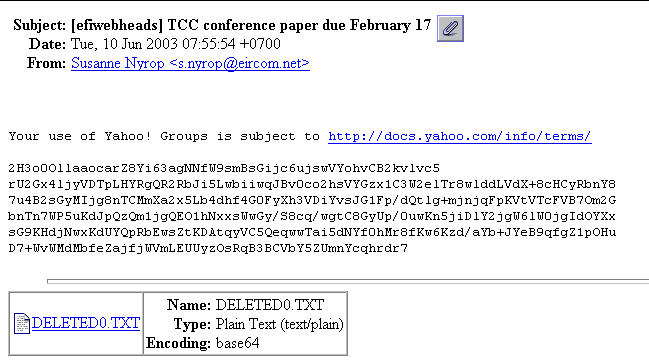
Info on sobig http://securityresponse.symantec.com/avcenter/venc/data/w32.sobig.c@mm.html
From address: is a trusted source, from your, or a familiar, address list
Subject: The subject line will be one of the following:
Message Body: Please see the attached file.
Attachment: The attachment name will be one of the following:
document.pif NOTE: The worm de-activates on June 8, 2003, and therefore, the last day on which the worm will spread is June 7, 2003.
Worm.ExploreZip
What to do about it: Ad-aware can be downloaded for free from http://www.download.com, http://www.softonic.com. Zone Alarm suppresses ads and popups and spyware, letting you know when the latter are sending data to and from you computer.
Be wary of Gator: You do NOT want Gator on your computer. I have found that Tripod tries to install it on my computer, but it asks first, so you have to be alert. Here's what Gator does, or tries to do ...
The other day, in the course of surfing, I was asked if I would 'always trust' content from (probably Gator) and being in the middle of multitasking, I clicked OK and then happened to notice that a 'Precision' product installed on my computer. When I went to uninstall it, it wasn't there, but digging into docs for it, I found that it would likely take some time for the product to install to the point where it would appear in the add/remove programs menu.
Later, I checked my add/remove programs again and found this time that Precision was there, and also Date Manager. I removed both and then as suggested searched my computer for 'gator'. I found 6 files, 2 cookies and 4 log files. I was able to remove all without ending any processes. I rebooted and none of this stuff is there any longer.
Here's how to get rid of this stuff
|
For comments, suggestions, or further information
on this page Last updated: January 13, 2008 10:00 UTC |
Copyright 2008 by Vance Stevens
under Creative
Commons License: http://creativecommons.org/licenses/by-nc-sa/2.5/![]() January 16, 2007
January 16, 2007
Mirrors: This page is available at: